Online Training Course
ISACA CISM
CyberVista’s CISM Training Course enables experienced practitioners to participate, learn, and partner with other professionals as they prepare to earn the highly in-demand CISM certification.

Who should earn the CISM
The CISM is an advanced certification designed for experienced practitioners, managers, and executives. It covers a wide range of cybersecurity topics from a governance perspective. The CISM also meets the U.S. Department of Defense Directive 8570/8140.
Chief Information Security Officer
Security Manager
Director of Security
Security Auditor
IS/IT Consultant
Information Security Manager
Security Systems Engineer
Security Consultant
Course Overview
ISACA’s CISM (Certified Information Security Manager) certification is a management-focused certification designed for professionals who design, build and manage enterprise information security programs. Achieving this leading information security credential will help you join a growing and elite network.
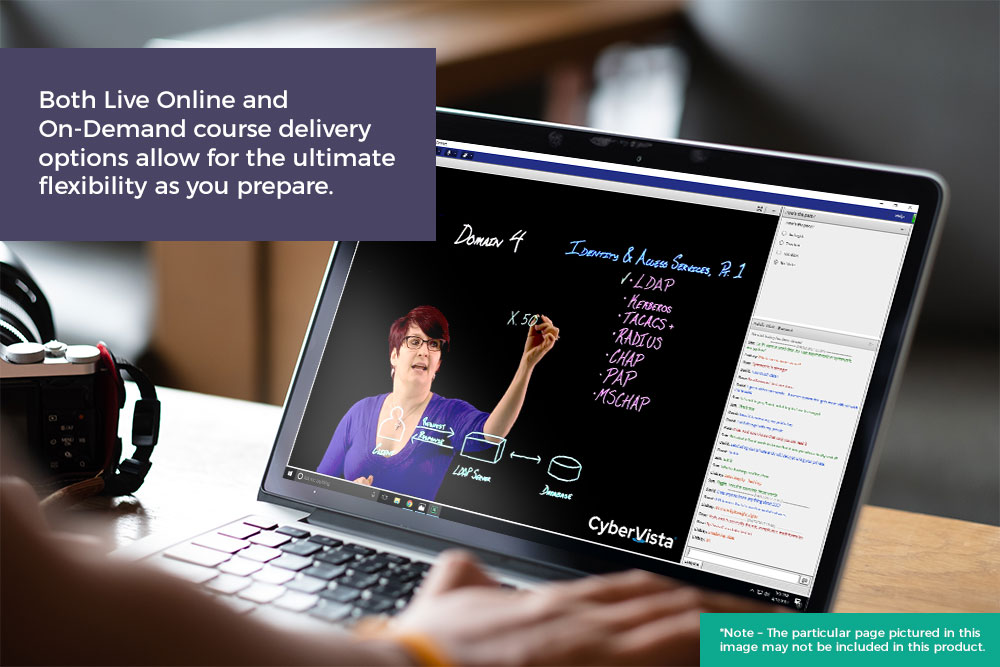
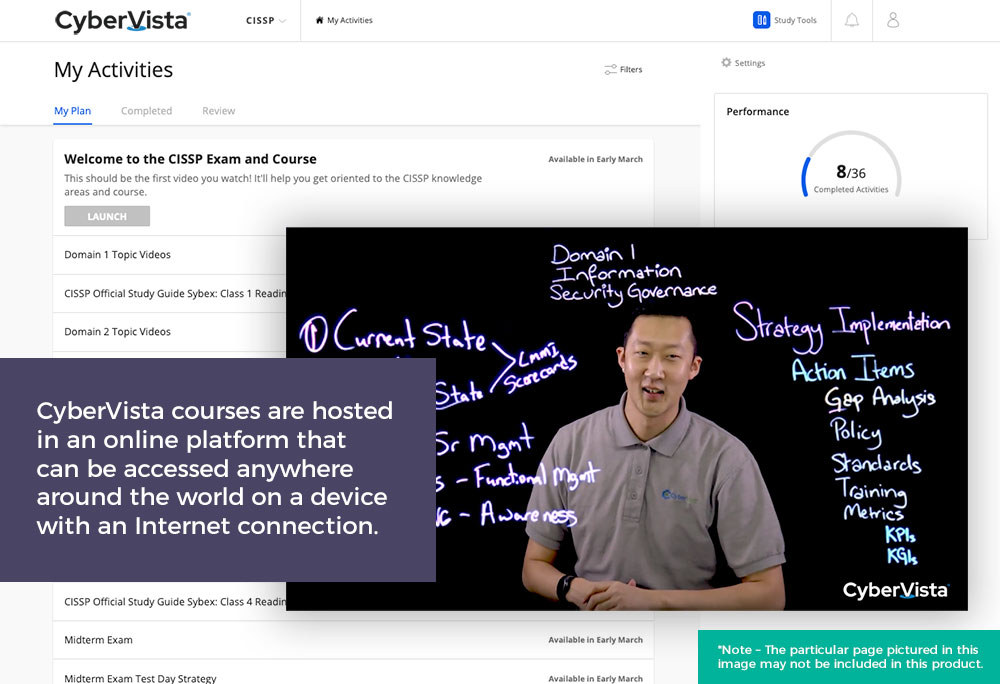
As an official training provider for ISACA, we offer CISM as a Video On-Demand Course that allows participating practitioners to move at their own pace.
Readiness guarantee – CyberVista offers a course readiness or retake guarantee on all Certify courses. If any individual taking this training course does not pass the exam on the first try or does not feel prepared following the completion of the course can retake the course at no additional charge for up to one full year.
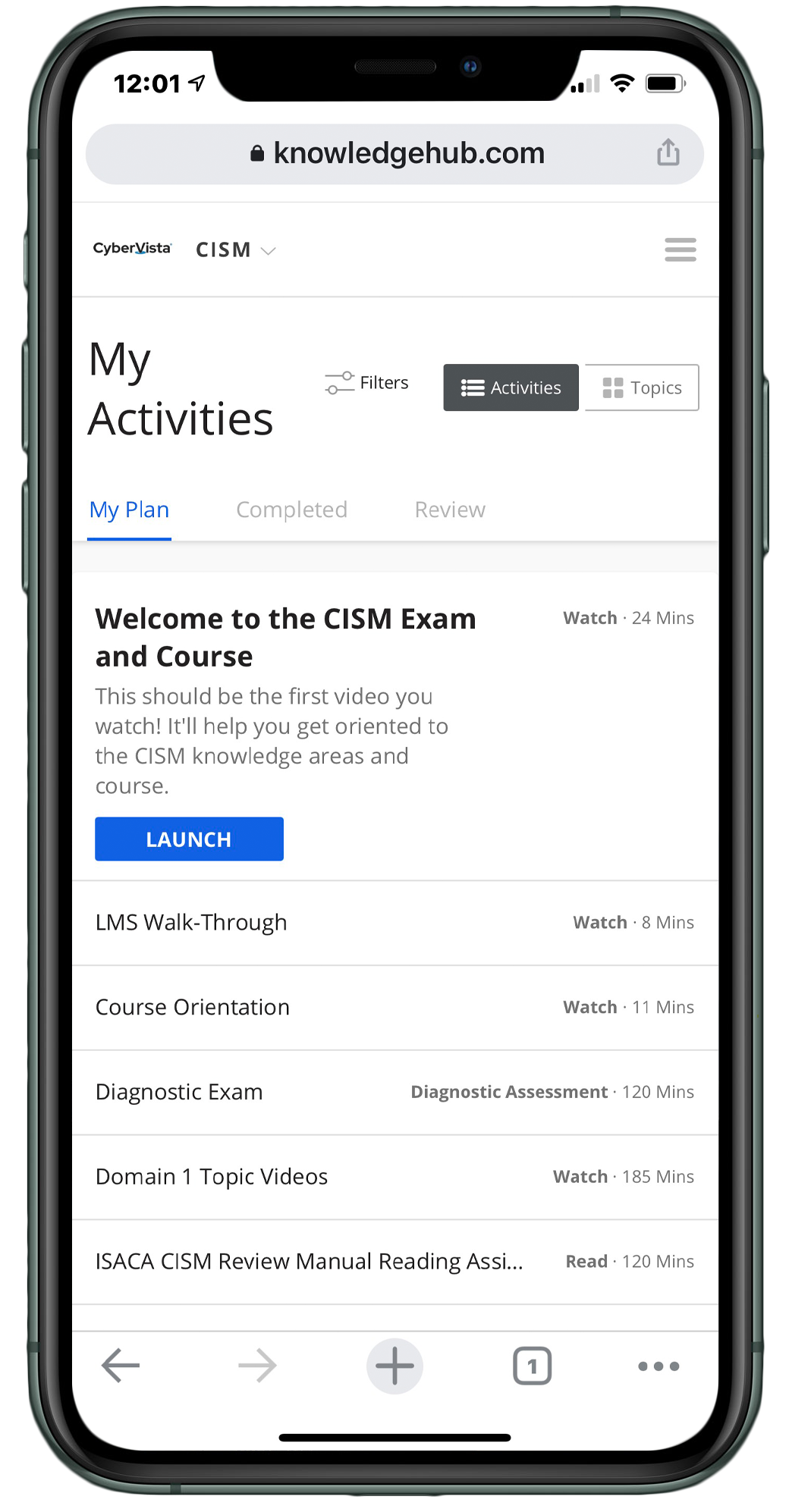
This course includes:
- 16+ hours of 5-15 minute on-demand training videos
- Supplementary videos
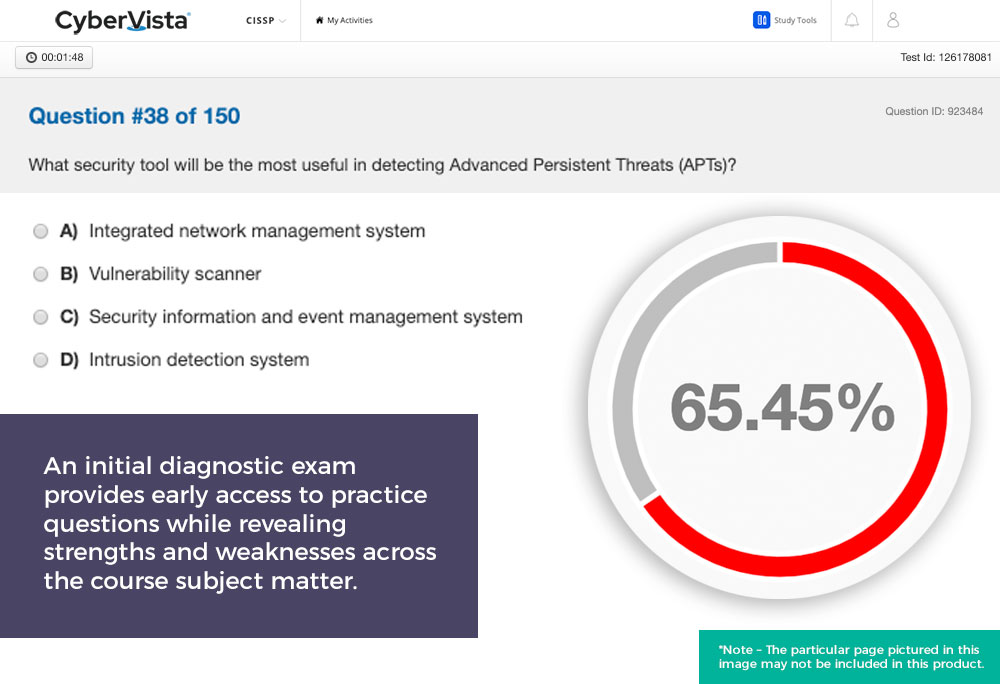
- 100 question diagnostic exam
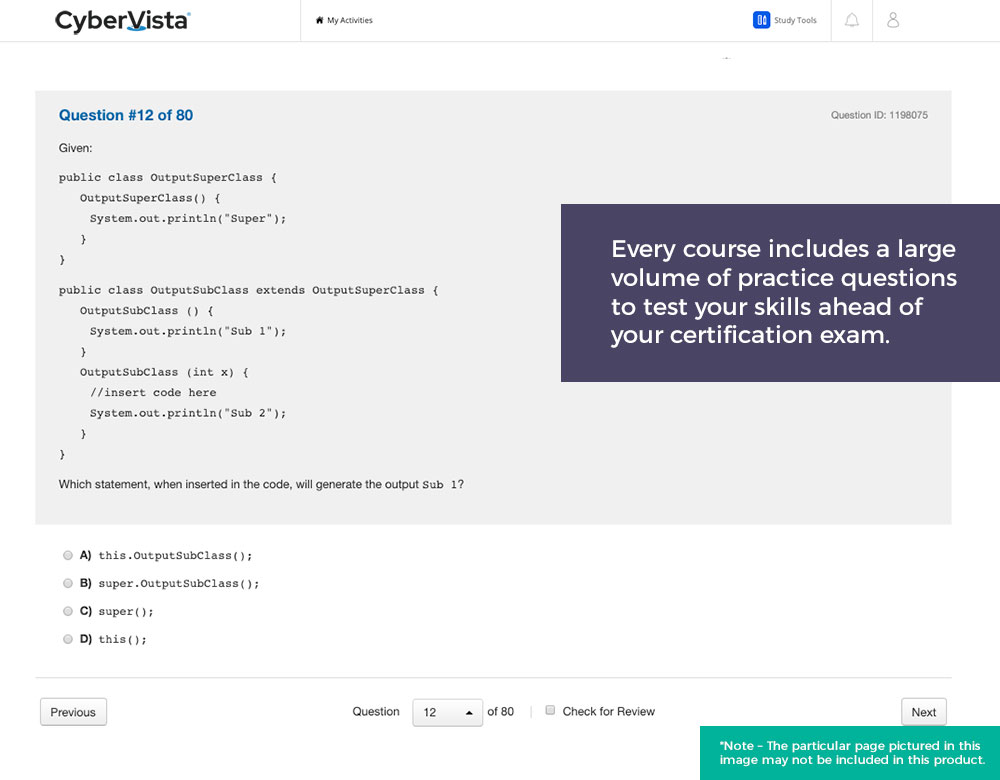
- 950+ practice question bank
- 400+ digital flashcards
- 100 question mid-term practice exam
- 150 question final exam
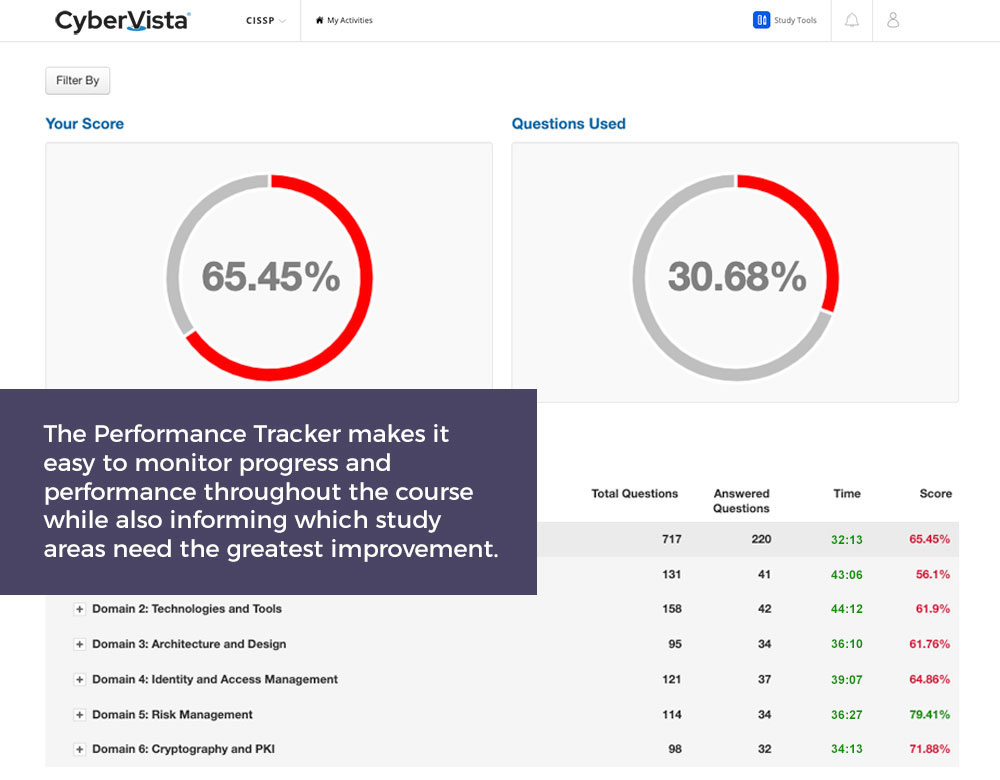
- Performance Tracker
- Summary Notes
- Summary Videos
- CISM Review Manual (15th Ed.) by ISACA
Course Outline
Domain 1: Information Security Governance
- 1 Introduction
- 1.1 Information Security Governance Overview
- 1.2 Effective Information Security Governance
- 1.3 Roles and Responsibilities
- 1.4 Risk Management Roles and Responsibilities
- 1.5 Governance of Third-Party Relationships
- 1.6 Information Security Governance Metrics
- 1.7 Information Security Strategy Overview
- 1.8 Information Security Strategy Objectives
- 1.9 Determining the Current State of Security
- 1.1 Information Security Strategy Development
- 1.11 Strategy Resources
- 1.12 Strategy Constraints
- 1.13 Action Plan to Implement Strategy
- 1.14 Information Security Program Objectives
Domain 2: Information Risk Management
- 2 Introduction
- 2.1 Risk Management Overview
- 2.2 Risk Management Strategy
- 2.3 Effective Information Risk Management
- 2.4 Information Risk Management Concepts
- 2.5 Implementing Risk Management
- 2.6 Risk Assessment and Analysis Methodologies
- 2.7 Risk Assessment
- 2.8 Information Asset Classification
- 2.9 Operational Risk Management
- 2.1 Third-Party Providers
- 2.11 Risk Management Integration with Life Cycle Process
- 2.12 Security Control Baselines
- 2.13 Risk Monitoring and Communication
- 2.14 Training and Awareness
- 2.15 Documentation
Domain 3: Information Security Program Development and Management
- 3 Introduction
- 3.1 Information Security Program Management Overview
- 3.2 Information Security Program Objectives
- 3.3 Information Security Program Concepts
- 3.4 Scope and Charter of an Information Security Program
- 3.5 The Information Security Management Framework
- 3.6 Information Security Framework Components
- 3.7 Defining and Information Security Program Road Map
- 3.8 Information Security Infrastructure and Architecture
- 3.9 Architecture Implementation
- 3.1 Security Program Management and Administrative Activities
- 3.11 Security Program Services and Operational Activities
- 3.12 Controls and Countermeasures
- 3.13 Security Program Metrics and Monitoring
- 3.14 Common Information Security Program Challenges
Domain 4: Information Security Incident Management
- 4 Introduction
- 4.1 Incident Management Overview
- 4.2 Incident Response Procedures
- 4.3 Incident Management Organization
- 4.4 Incident Management Resources
- 4.5 Incident Management Objectives
- 4.6 Incident Management Metrics and Indicators
- 4.7 Defining Incident Management Procedures
- 4.8 Current State of Incident Response Capability
- 4.9 Developing an Incident Response Plan
- 4.1 Business Continuity and Disaster Recovery Procedures
- 4.11 Testing Incident Response and Business Continuity/ Disaster Recovery Plans
- 4.12 Executing Response and Recovery Plans
- 4.13 Post Incident Activities and Investigation
I’ve attained my share of certifications, and this CEH course was among the best exam prep classes that I’ve ever taken. The pacing and presentation of the content felt very much like a college class, which really aided in effective retention and understanding of the information.
The online resources that are available are also incredibly useful, especially the library of practice questions. Overall, this course would have been a worthy use of my time even if there were no test associated with it, which is the highest praise I can give a training program.I took the Certified Information Security Manager (CISM) course with CyberVista and was extremely surprised at how they captured all the key points and presented it to students using an easy to follow format. The instructor was amazing! His energy level seemed to power the lightboard at times. The information was well organized, concise, and in-depth during our class. I currently hold an ISACA certification and I am prepared to take the CISM to advance my cyber security career.
CyberVista CISM Courses are great for the working professional. You can take the classes with you in the car, office, or from the house. When taking the course from a computer, you can interact with the instructor, ask questions, chat with your classmates and CyberVista provide breaks as if you were sitting in an actual classroom.
Expect homework. When you start the class you will take a pretest to assess your current skills, every week you will complete a test, and you will have both a midterm and a final exam. CyberVista wants each student to succeed and provides supplemental learning material on areas former students have struggled with learning. Oh and don’t forget the homework which is videos covering the same topics as the course presented in a slightly different way to help the material stick. CyberVista Courses are the most realistic class you can take and still be in the comfort of your own home.I recently completed the online CISM course offered through Cybervista. I have had experience taking other courses through the government, academic institutions and other large international vendors and I can emphatically say that I have not been better prepared or more confident in taking an associated certification than with the CyberVista program.
The instructor was not only knowledgeable, but possessed the ability to convey the information in academic terms and from personal experiences. The content was well organized and thorough. The books were designed to really aid the student in putting the pieces together. The virtual classroom was cutting edge and first rate technology. Real time feedback, real time question and answers and quizzes. The staff had respect for those in the class who had other experiences and solicited others opinions.. I don’t see myself attending any other training at this point other than CyberVista."I would not have passed the CISSP exam without Cybervista! The instructors were knowledgeable and helpful in grasping the material... The weekly online lessons were extremely helpful in breaking down each of the domains covered on the exam. If you follow the study plan provided and put in the time required to understand the major concepts outlined by CyberVista, you’ll pass!"
"When I was training I found myself using CyberVista’s quiz bank a lot, plus they tested me in other ways such as the initial diagnostic exam, the midterm, and the final exam. Getting used to the wording and doing all those practice questions helped me prepare. There was also a system at CyberVista for figuring out my strengths and weaknesses – it honed in on the areas I needed to study more."
"Before CyberVista I was given an opportunity to attend a one-week boot camp. Since my employer was paying for it, I did not hesitate to take advantage of the offer. After that one-week boot camp, I came out of there with more questions than I had going in. I did not feel prepared and the training just simply wasn’t enough. CyberVista’s curriculum is an integration of live online lectures, on-demand videos, and an array of self-study tools–it was just what I needed."
"I can’t afford, time-wise, to sit in a classroom for a whole week. Being able to watch the class, and participate, while trying to put my daughter to sleep, was a big boon. Also, the class was organized really well. The multiple online quizzes that we were able to take, and then learn what areas we needed to study more, was really helpful. Also, the light board technology was great. I found it captivating, and it was actually the reason why I signed up in the first place."
"This was my first time studying for a certification through live online training. There were definitely benefits to taking a live online class. For example, you can take your classes from anywhere with an internet connection. I’m happy the training was spread out leveraging multiple learning tools. It was the balance of all of those different aspects that helped to reinforce concepts and instill a strong comprehension of the CISSP."
"I started with a free self-study course and quickly found the accountability was missing. CyberVista’s live interactive course using the light board was a first for me and a great experience overall. It kept me accountable and engaged. The real-life experience of the instructors was evident and their ability to articulate concepts was great. The value of interacting with other students in this live environment was also a significant benefit. It’s not easy getting folks to participate, but CyberVista made it happen."