N2K Incident Response Training Course
Build and enhance incident response skills.
Enterprise organizations are bombarded by cybersecurity attacks on a daily basis. It’s not a matter of if a breach will occur; rather it’s a question of when and to what extent. Incident Response teams can work quickly to contain and mitigate a breach. Yet, upskilling individuals to act in a full IR capacity is not an easy task. The industry doesn’t yet offer an incremental learning path from a SOC Analyst or Cybersecurity Specialist role directly feeding into IR.
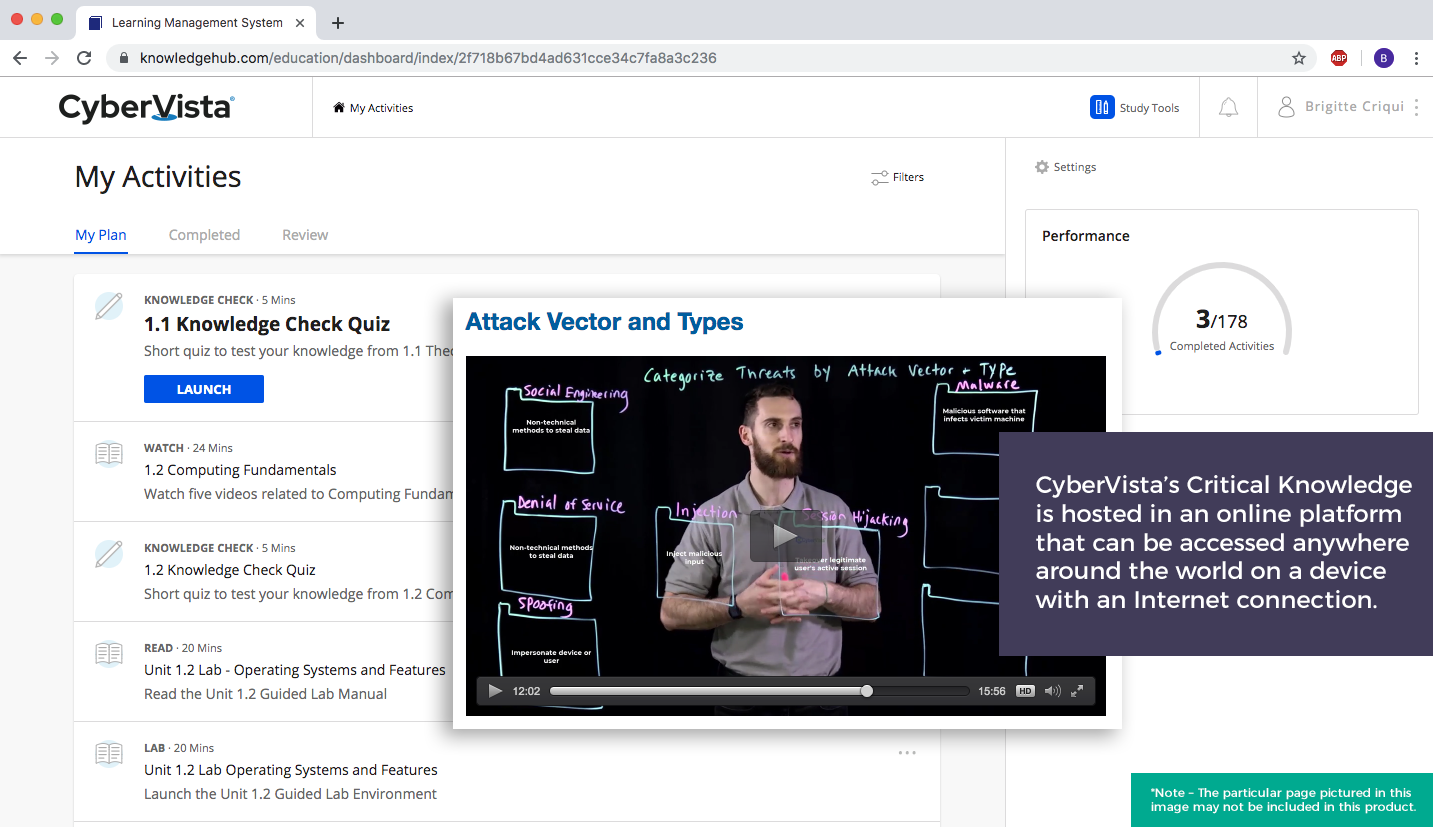
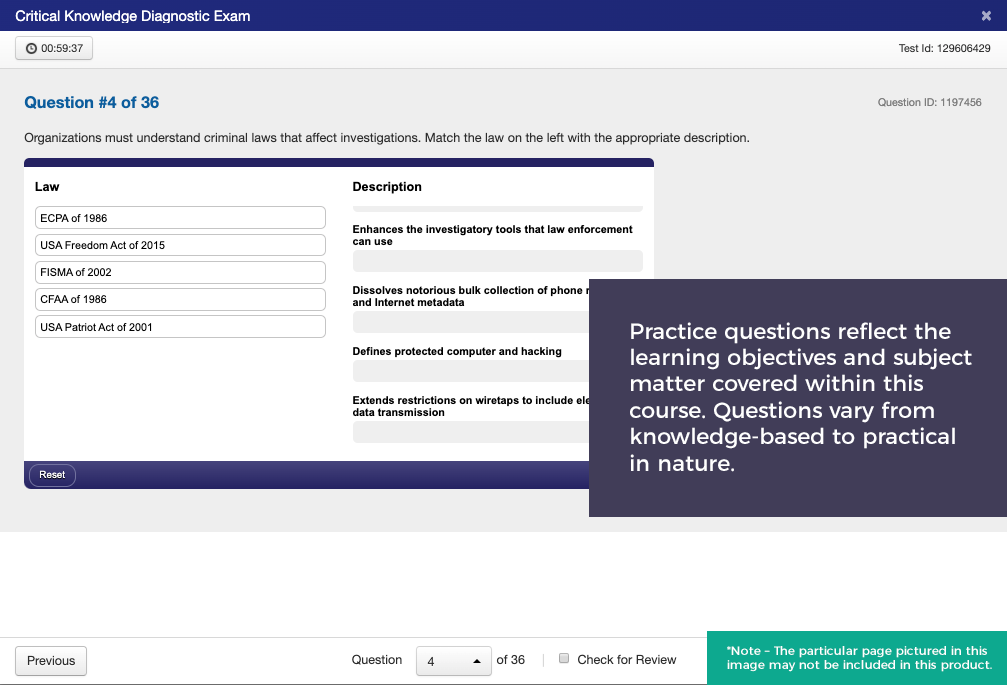
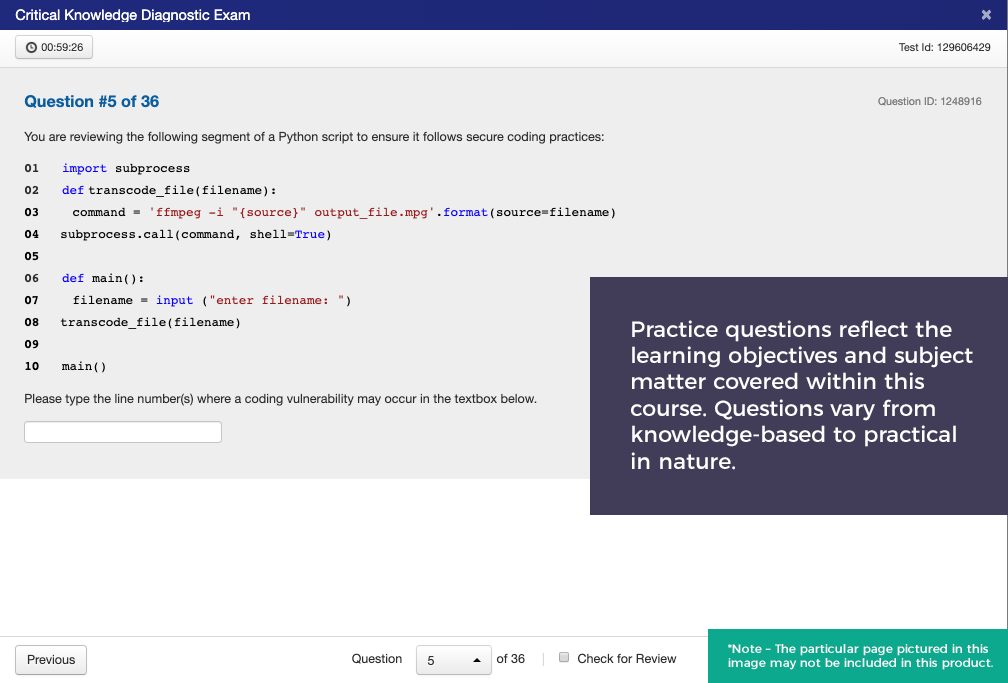
CyberVista now offers a 100% online training program designed to develop Incident Responders quickly and cost effectively. N2K’s Incident Response course is a comprehensive offering that builds on the Critical Knowledge training program. This course goes beyond fundamental concepts and dives into technical and task-oriented subject matter designed specifically for Incident Responders. Team members working within a CERT (computer emergency response team), CSIRT (computer security incident response team), CIRT (computer/cybersecurity incident response team), or broader SOC (security operations center) would benefit greatly from this course.
Unit 0: Foundational Knowledge
Learners will establish or revisit foundational concepts necessary to building knowledge and skills in later units.
- 0.1 Networking Basics
- 0.2 Host Basics
- 0.3 Indicators of Compromise
Unit 1: IR Overview
Learners will understand various roles within an organization and their responsibilities prior to, during, and after an incident occurs.
- 1.1 Incident Response Overview
- 1.2 Roles and Responsibilities
- 1.3 Policies and Procedures
Unit 2: Attack Lifecycle
Learners will understand the Cyber KillChain and the Mitre Attack Framework. These are important to understanding the phases of an attack and how to determine a resolution.
- 2.1 Cyber Kill Chain
- 2.2 Mitre Attack Framework
Unit 3: Host and Network-Based Detection and Resolution
Learners will become familiarized with means of detection and resolution of network intrusions and malware attacks.
- 3.1 Network Analysis and Attack Identification
- 3.2 Host and Network Intrusions
- 3.3 Malware and Rogue Device Detection
Unit 4: Attack Patterns and Mechanisms
Learners will be able to understand attacks listed in the OWASP Top Ten, the methods that these attacks propagate and affect an organization, and remediation techniques.
- 4.1 Network-Based Attacks
- 4.2 Host-Based Attacks
- 4.3 Attack Methods
Unit 5: Forensics
Learners will become familiar with digital forensics, techniques used, case studies, and additional hands-on exercises.
- 5.1 Forensics in IR
- 5.2 Forensics Methodologies
- 5.3 IR Case Study
- 5.4 IR Activity