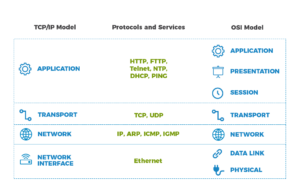
Network protocols are a set of rules that establish how network devices process information and communicate. They are crucial to how devices communicate and function. One of the most important network protocols is NTP, or Network Time Protocol.
NTP
The Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in current use. NTP is intended to synchronize all participating computers to within a few milliseconds of Coordinated Universal Time (UTC).
Why do we need it?
All infrastructure devices such as firewalls, routers, and switches have logs where events of various types are recorded. These logs can contain information valuable for troubleshooting both security and performance of systems. You can direct these event messages to a central server, called a syslog server. By doing so, you create a single system for access to all event logs. A Syslog Server also makes it easier to correlate events on various devices by combining the events into a single log. To ensure proper sequencing of events, all devices should have their time synchronized from a single source using an NTP server.
How does it work?
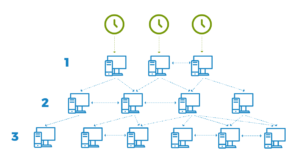
NTP uses a hierarchical, semi-layered system of time sources. Each level of this hierarchy is termed a stratum and is assigned a number starting with zero for the reference clock at the top. A server synchronized to a stratum n server runs at stratum n + 1. The number represents the distance from the reference clock and is used to prevent cyclical dependencies in the hierarchy. Stratum is not always an indication of quality or reliability; it is common to find stratum 3 time sources that are higher quality than other stratum 2 time sources.
Stratum 0
These are high-precision timekeeping devices such as atomic clocks, GPS or other radio clocks. They generate a very accurate pulse per second signal that triggers an interrupt and timestamp on a connected computer. Stratum 0 devices are also known as reference clocks.
Stratum 1
These are computers whose system time is synchronized to within a few microseconds of their attached stratum 0 devices. Stratum 1 servers may peer with other stratum 1 servers for sanity check and backup. They are also referred to as primary time servers.
Stratum 2
These are computers that are synchronized over a network to stratum 1 servers. Often, a stratum 2 computer will query several stratum 1 servers. Stratum 2 computers may also peer with other stratum 2 computers to provide more stable and robust time for all devices in the peer group.
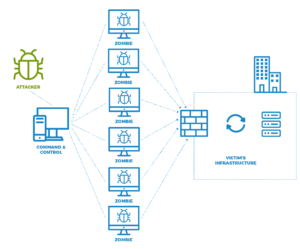
NTP server misuse and abuse
Because NTP is such a crucial and commonly used protocol, it’s a prime target for attackers. NTP server misuse and abuse cause damage or degradation to a NTP server. This is usually either violating the NTP server’s access policy or flooding it with traffic, carrying out a Denial of Service (DoS attack). A denial-of-service attack (DoS attack) is an attack in which the perpetrator floods the targeted machine or resource with unneeded requests in order to overload the systems and prevent all real requests from being fulfilled.
Want to learn more?
Are you looking to up your cybersecurity game and earn your next certification? Or maybe you manage a team that needs a more efficient, effective and less expensive way to train? Whether you are looking to train your C-Suite, yourself, or your team, we’ve got you covered —with learning delivered by experts in bite sized pieces, 100% online.