Did the New Press Secretary Tweet His Password?
This post is part of a series in which we pull security stories right from the headlines and discuss their relevance to the eight domains of the CISSP® exam.
Read our previous posts in this series:
Name That Domain: Backdoors
Name That Domain: Ransomware
Name That Domain: Data Breaches
Name That Domain: Risk Management
Mysterious Missives Prompt Security Dialogue
We’ve all posted something on social media that we wish we could take back –an unprofessional tweet, perhaps, or a dramatic rant about how overrated La La Land was (@RyanGosling). Sean Spicer, the new White House Press Secretary, recently found himself in this situation. Spicer issued this curious tweet from the official @PressSec account last week:
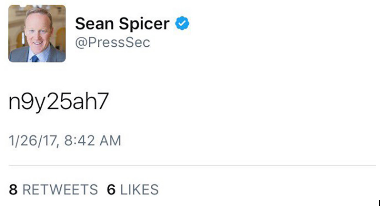
Spicer’s followers were puzzled, but many speculated that he had accidentally tweeted out his password. If this string of characters was indeed Spicer’s Twitter password, the CISSP candidate would have something to say about it.
Domain 5: Identity and Access Management
CISSP candidates learn in Domain 5 what makes a strong password. Spicer’s (maybe) password is solid, but it could use improvement. Let’s start with the positives: The password appears to be random. It uses a mix of numbers and letters. It doesn’t appear to have any connection to Spicer himself, meaning it avoids using his name, phone number, date of birth, address, dog’s name, and mom’s name.
Now let’s move to areas of improvement. The first issue is that it’s too short. Password length is one of the most influential factors that determines its security. In fact, password cracking technologies, known as brute force tools, can crack a complex, five-character password in less time that it takes to fire a tweet (about a minute). However, a complex, 12-character long password takes thousands of years to crack. Spicer’s eight character password is better than five, but he should aim for 15 when making his new one.
Another issue with the password is that it doesn’t utilize special characters. It has numbers and letters, but to be truly complex, it needs special characters such as #, %, *, !, ,, and +.
A final, fundamental issue with the password is that it isn’t a passphrase. A passphrase is also a random string of characters, but it has unique meaning to the owner. Passphrases are easily created by injecting special characters into familiar phrases or sentences. For example, “alternative facts” may be converted to: “@1t3rn@1!^3+f@ct5”.
Passphrases are beneficial because they include complex characters that are hard to brute force, yet they are easy to remember. This means users are less likely to write them down. (We wonder where Spicer has his passwords written down). This is crucial because if your password is anywhere besides in your head or a secure password manager, it is not secure. When you write down your password, you expand your attack surface. If Post-it note reminders under the press conference podium are your security standard, then hackers will find a way to exploit it, either through either through deception, trickery, or physical intrusion.
A Helpful Tweet
We will probably never know if Spicer tweeted (or “butt-tweeted”) his password. Regardless, we hope the mysterious tweet starts a conversation about security, instead of just giving the Internet more fodder for political comedy.


