CyberVista + Dell: A New Model of Cyber Workforce Development
No one in cybersecurity enjoys the hiring process. Employers with countless open positions to fill are faced with dozens of resumes filled with certifications but little tangible evidence of being qualified to perform the job. Candidates are frustrated because they’ve invested time and money in their education but often find they can’t get past an initial screening interview. The standard thinking that job prospects can be gained largely through certifications no longer applies, but the roles that so desperately need to be filled are not clearly defined.
What if there was a way to change the paradigm to solve this problem? Instead of relying on academics and training providers to divine the up and coming skills in the cybersecurity industry, what if employer demand for role definitions and job functions drove hiring requirements as well as an organization’s training curriculum?
With this premise, Dell and CyberVista partnered to try and improve the process. Dell’s understanding of the underlying skills within its cybersecurity enterprise was fundamental to developing a human capital management plan for the company’s current and anticipated cyber staff. The project started with an inventory of Dell’s current cybersecurity job roles, clarifying its internal hierarchy, reviewing job families and examining what makes each role different. Based on the results of this inventory, CyberVista developed a list of required skills for each job role, weighted and ranked the most critical skills, and grouped them by career level. The initial analysis helped CyberVista develop a roadmap of cyber career pathways as well as informed the creation of a training framework that not only would teach the conceptual and practical skills needed to perform the duties of a particular role, but also give aspiring or transitioning cybersecurity talent actionable direction and efficient interventions for advancement.
Evaluating Dell’s Workforce
If you are going to fundamentally rework your workforce plan, you first have to figure out the status of your company’s department. Conducting an overhaul is not an easy or quick process — especially for a company like Dell. Dell employs 145,000 people across the world, with more than 400 in its cybersecurity department.
Looking across its cybersecurity department, Dell determined that people were the most significant risk, not tools and technologies. So the management team asked itself what it could do invest in its employees and created a thoughtful workforce plan.
There was a lot of internal information to process before Dell could even begin to find answers. The organization wanted a hiring framework based on data, current roles, accurate job families, and mobility within career paths. And accomplishing all this was not a one-person effort. The cybersecurity team needed to partner with its HR department to ensure the new model fit within the overall Dell company culture.
Like any new initiative, there were challenges. Dell needed to create new job families and ran into resistance as some of its employees felt their roles were so unique and specialized that they could not be codified in something akin to a job role. The company eventually settled on definitions that characterized professionals as either physical security or cybersecurity. From there it created titles, pay bands, and other necessary labels for HR. But this was only the first part of the process.
The challenges didn’t stop there. While Dell had 400 cybersecurity professionals on staff, it still needed to hire another 150. While working with CyberVista to understand Dell’s existing workforce and future requirements was a step towards understanding the competencies needed in these roles, Dell’s HR department still needed reliable data to approve the changes. HR couldn’t create job families and pay bands without relevant definitions and external baselines for salary data.
How Did Dell Do It
Working with CyberVista and the results of its workforce analysis, Dell was able to create a structure and define job roles inside its cybersecurity organization. While the common lexicon of the National Initiative for Cybersecurity Education (NICE) and the National Cybersecurity Workforce Framework (NCWF) provided a good baseline, Dell and CyberVista worked together to ensure that any market taxonomy or skills profiles needed at the company were useable. From there, they were able to create a roadmap for requirements and skills.
Using the NCWF framework, CyberVista and Dell worked together to identify, aggregate, and audit all their cybersecurity job roles and postings in order to inform job descriptions, HR management, and future staff training requirements. We accomplished this by:
- Conducting a job inventory. Dell reviewed its 400 existing jobs and identified the roles it planned to prioritize and hire for existing restructuring and future hiring initiatives (in anticipation of the goal to bring on an additional 150 employees). Dell updated job responsibilities, many of which were written a decade ago.
- Identifying skills in cyber job roles. Dell and CyberVista worked together to conduct a thorough analysis of the roles by interviewing stakeholders across various cyber business units. CyberVista used the feedback from this process to try and understand the nuances of the different roles. For example, how different is a malware analyst really from a forensic analyst?
- Evaluating market trends. Dell was also realistic in setting the expectation that the market landscape, trends, and job hierarchy of the future were critical to the long-term success of the cyber group. It evaluated market landscape and trends that informed the next set of cyber talent solutions and provided a career investment tool for solution.
- Hosting alignment sessions with partners and its consultant. Dell engaged with external HR market intelligence and specialist teams to understand market salary trends and benchmarks across the industry. CyberVista also engaged with these partners to provide skill and competency input to refine the models.
New Job Families and Better Reporting
In the end, the process created five additional cyber job families, allowing Dell to build compensation and hiring plans more aligned with specialized roles. Dell formed them by considering roles that are the most difficult to fill within their organization and its risk landscape. Job functions like digital forensics, incident response, and cybersecurity consulting were identified. In addition to the functional job families, Dell also created a leadership role based on the business skills required within in cyber management.
The process impacted more than 460 team members and its market intelligence team priced 44 new jobs.
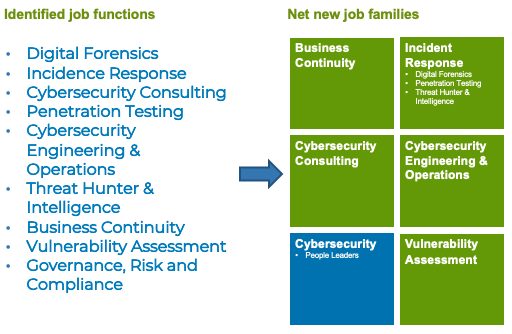
Moving forward, Dell will continue to monitor the market for trends and continue to refine the job family structure. It plans on using the detailed skill taxonomy CyberVista was able to create to provide performance based career mobility, identifying skills gaps and establishing training plans for staff to upskill or reskill between job roles. Finally, Dell is working to create a diverse pipeline of security professionals starting at the most junior levels who will have a clear pathway and training options for advancement within their organization.
Improving Cybersecurity Education
Dell’s approach provided an opportunity for CyberVista, which had already been working toward an employer-driven model of cybersecurity training and education. We believed actual job functions and requirements should drive curriculum and training requirements, and most of the current cyber training offerings catered to existing workers with cybersecurity skills but often fell short when trying to identify and pipeline new sources of talent.
Working with Dell, CyberVista was able to capture real-world data on the skills, knowledge, and abilities that cyber employees need to demonstrate to be successful in their roles. By synthesizing this data within each job role and family, we were not only able to document the foundational, specialized and on the job skills required within each role, but also we were then able to analyze the gaps to identify career, skill, and training pathways for cyber professionals. The knowledge gained from this project helped us create a detailed taxonomy that aligns to the NCWF but also serves as a roadmap to identify the skill and knowledge gaps between the roles and levels.
What CyberVista Gleaned for Training Development
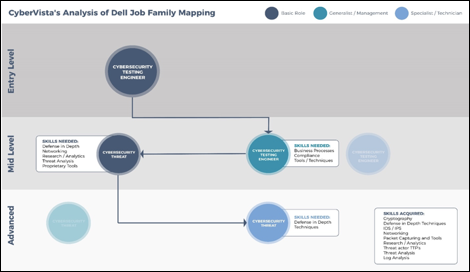
Working with Dell, CyberVista was able to achieve our goal of creating and deploying a flexible framework employers could use to measure, guide, and develop their cyber teams. Whether Dell, or any other employer, chooses to use that framework by identifying talent from adjacent roles to reskill into cyber roles or to provide professional development opportunities and a career path that increases retention is totally up to them. The beauty of a model like this is that it provides a picture of how an employee’s career path could progress. For example, there are different skills or competencies needed as a technical specialist versus a leadership role. Once we were able to identify and validate the skill requirements needed for each job, it was much easier to then determine skills overlaps and skill gaps for each role.
CyberVista’s ability to map the skills and knowledge an employee would need to master to transition from one role to the next in their actual job environment was one thing. But the more exciting conclusion from our perspective was that now there was real-world data that we could use to build training and education to close the gaps between different skills in a targeted, modular, and efficient way.
Because the framework we built for Dell was based on an underlying taxonomy of skills, it didn’t matter that Dell might have slightly different job role definitions than another employer. Since we thought through skills from the broadest domains (i.e. networking) all they way through the most detailed skills within them (i.e. subnet implementations), employers can configure and define competencies for job roles based on their own unique cyber organization. Instead of having to rely on a one-size-fits-all approach, this framework helps employers breakdown the fundamental skills an employee needs for each role within their own company, including skills that would be nice to have and those that can be learned on the job. A SOC analyst in one organization, as an example, may require more investigative and discovery skills at a Tier 3 level versus another organization where they require more staff with foundational networking monitoring skills and knowledge.
If an employee wants to transfer to a new role, they’ll know exactly what skills they need to acquire. These training pathways give them a holistic way to move up their chosen career ladder. And further, the framework itself is flexible so an organization can either use CyberVista’s or customize it to meet their own requirements.
Building Better Cybersecurity Curriculum
For employees and employers, a more productive curriculum will help with training and hiring. There’s now a common core of cyber domains. Having a skills taxonomy that specifically breaks down to learning objectives is a new development in the fragmented training space, and this allows for a developed structure to build modular, bite-sized training for developing the skills needed for each role.
For example, training will now be aligned to company-specific job roles that can assess and support the professional development of staff. Companies will be able to evaluate new or current employees on specific skills.
Moving the Cybersecurity Training Industry Forward
The industry can start to move towards more professionalization with an employer-driven training model. New entrants and professionals alike can advance and pursue specializations by focusing on an actual training path.
CyberVista takes this taxonomy with skills required by role and delivers comprehensive training in a 100% online, modular and configurable platform. This training, using our proprietary learning formula starts with a diagnostic assessment to establish each student’s starting level and skills base. The training program then combines conceptual learning through video. We’ve applied the best of learning science to ensure that our video delivery is engaging, interesting, dynamic, and instructive. Finally, the experiential learning using scenarios and hands-on lab, allows students to reinforce their skills and knowledge by getting their hands on keyboards. This allows students to easily apply what they have learned to their jobs.
The future is finally here with next level training for aspiring and current cyber practitioners. We’ve created a curriculum and training platform based on employer needs. Want to learn more? Visit us at cybervista.net/advance and advance your organization.


