Ethical Hacking Tools You Should Use
We recently outlined what it means to be an ethical hacker and how individuals working as ethical hackers can rapidly bolster the security posture of their affiliated organizations. Now let’s dive deeper and review popular tools commonly used within the ethical hacking community.
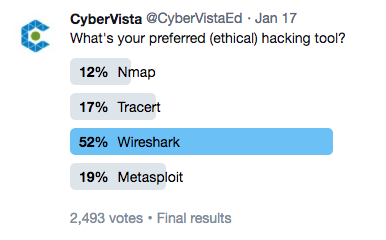
Although there are dozens of popular hacking and investigative tools out there, many of which are open-sourced, we asked our Twitter community to choose their favorite out of four widely-known options. Nearly 2,500 people voted and Wireshark emerged as the clear winner, earning 52% of the votes. Beyond preference, we’re going to cover why these tools (and a couple of others) are instrumental to the daily grind of an ethical hacker.
Nmap

Nmap (“Network Mapper”), often referred to as the Swiss Army knife of security scanning, is an open-source and free command line security tool. It’s typically used to discover hosts and services on a network and enumerates the services and hosts. It’s commonly used for penetration testing and security auditing.
How it works: Nmap uses raw packet data in unique ways to discover what other hosts are available on the network, what services those hosts are positioning, what operating systems (and OS versions) they’re running, and what kind of packet filters and firewalls are currently in place.
Why is it useful? Nmap is an essential tool for penetration testers, network administrators, systems administrators, and security auditors for vulnerability identification within their own systems. Ethical hackers think of Nmap as the main determinant of a port availability, as well as discovery of hosts and services on a network.
Tracert or Traceroute

Tracert (Windows-based) or Traceroute (Linux-based) is a command line tool that monitors the trail of a packet across the Internet and provides the path of that packet along with its transit times. This tool precisely determines how data, such as a Google search query, travels from your network to another network by revealing the hop points a packet will travel. Tracert assists ethical hackers by gathering information about a specific network’s infrastructure and its IP ranges.
How it works: Tracert tracks the packet using ICMP ECHO packets to report information on each router from the source to the destination. Matt Walker’s CEH Certified Ethical Hacker All-in-one Exam Guide, explains “the TTL on each packet increments by one after hop (router) is hit and returns, ensuring the response comes back explicitly from that hop and returns its name and IP address.”
Why is it useful? Tracert and Traceroute are not a “hacking” tools; however, they are commonly used investigative tools and have grown popular in the ethical hacking community. The main convenience of Tracert is that it compiles a list of the IP address of each computer/server. Therefore, if there is an interruption during a data transfer, this tool can show you where the problem occurred along the chain. Tracert is useful for determining where specific packets of data may be getting caught, or stopped on the network. Users may also want to use Tracert and Traceroute to identify firewalls that may be blocking ICMP traffic. If an ethical hacker learns that a firewall is blocking incoming ICMP traffic they know they will need to use other tools to try and test the network.
Wireshark

Wireshark is an open-source, free network packet analyzer, used to capture and analyze network traffic in real-time. It’s considered one of the most essential network security tools by ethical hackers. In short, with Wireshark you can capture and view data traveling through your network.
How it works: Many people gravitate towards Wireshark’s robust GUI, used for packet capturing and analysis. Packet Analyzers operate by allowing a user to put network interface controllers (NIC’s) in promiscuous mode in order to view and capture network traffic. For instance, packets that are captured through Wireshark are filtered into data streams, paths, protocols, and IP addresses to be analyzed and studied in greater detail.
Why is it useful? There’s a reason Wireshark was the winner of our poll. It’s frequently used for troubleshooting network performance, identifying unusual traffic, firewall bleed, misconfigured software, and protocol issues. Ethical hackers will use network protocol, and packet analyzers, such as Wireshark, to understand a target network on a granular level. Understanding how specific hosts and devices communicate on a target network is critical for proper vulnerability identification and penetration testing.
Metasploit

Metasploit is widely-known for its open-source “Framework” command line tool, and it’s considered one of the best hacker software tools available. Metasploit Framework testing platform allows users to write, test, and execute exploit code. It accomplishes these tasks by using a suite of tools that provide the ideal environment for penetration testing and exploit development.
How it works: Exploiting vulnerabilities using Metasploit’s Framework is done through a sequence of commands that are carried out by its built-in suite of tools and modules. The Exploit, one of Metasploit’s many modules, is the software that will be applied to the compromised network and provide access information of the target system to the Certified Ethical Hacker. Then, Metasploit boasts another module known as The Payload, which is “the actual code that executes on the target system after an exploit successfully executes.” The Payload works to take advantage of the target system. Throughout the sequence of commands, the ethical hacker needs to glean and gather the data regarding the network systems’ vulnerabilities.
Why is it useful? Metasploit “safely tests the cyber defenses” of a company’s network systems. For example, a company would hire an ethical hacker to determine the security of their website or network systems. A white hat would resort to Metasploit to evaluate and judge the caliber of the company’s cybersecurity and how the cyber defenses that are already in place would stand against the methods of a threat actor.
Aircrack-ng

Aircrack-ng is a compilation of network tools to evaluate wireless network security. Aircrack-ng can be run on Linux, OS X, and Windows operating systems as well as a few others. The suite of tools works with any wireless NIC and can sniff 802.11a/b/g wireless traffic.
How it works: To assess the security of the WiFi network, the software gauges the security of the network through four main activities: monitoring, attacking, testing, and cracking. Aircrack-ng uses brute force to guess the encryption key of a wireless service. One of the benefits of its toolset is it can use different techniques for cracking different encryption standards. Aircrack-ng isn’t a one-trick pony. It is a collection of tools including a sniffer, wireless network detector, a password cracker and a traffic analysis tool, all focused on cracking the encryption key to a wireless network. It can sniff for several types of wireless network security, including but not limited to WEP, WPA, and WPA2-PSK. For instance, Matt Walker’s text points out that “on WEP it can guess it’s encryption key by using the dictionary technique, PTW, FMS, and the Korek technique”
Why is it useful? Unsecured wireless networks are obvious and easy attack vectors for threat actors making it easy for them to compromise critical assets and personally identifiable information (PII). Wireless networks need to be secured and monitored for the same reasons you should change your passwords on a regular basis; to ensure confidentiality of data and to minimize the window of opportunity a potential threat has to manifest. Aircrack-ng is an essential tool for wireless vulnerability discovery, through the recovery of wireless keys, wireless packet capturing and injection, static WEP and WPA-PSK cracking, and by decrypting captured WEP/WPA files.
Maltego

Maltego “is an interactive data mining tool that renders directed graphs for link analysis. The tool is used in online investigations for finding relationships between pieces of information from various sources located on the Internet.” It probes the internet for information, makes sense of the data and helps connect the dots of its findings.
How it works: Maltego has the ability to perform link analysis, drawing the connections between one million entities of information on a single graph. Because the software finds the patterns and commonalities between the entities, the graphs, as a result, illustrate collections of nodes by grouping entities together. For instance, the NSA could track and monitor an enemy of the state. Once the investigative team discovers a piece of information regarding this person, such as a phone call, Maltego can probe the web and gather information regarding that person’s relationships, social media profiles, mutual friend, and employment history. This makes it much easier for an individual to find key relationships and links between data sources.
Why is it useful? The benefit of Maltego is that it has the capacity to analyze real-world relationships between separate pieces of open-source information. As a penetration tester, this can be an extremely useful tool in the footprinting and reconnaissance phase of the test. Gathering information on your target is important and often times we find ourselves missing pieces to the puzzle. By taking advantage of Maltego’s link analysis, further conclusions and associations can be made using information that may have previously been ambiguous or unknown. Maltego runs on Windows, OS X, and Linux operating systems making it a versatile tool for almost any organizational environment.
There’s More Where That Came From…
The world of ethical hacking is vast and we’ve barely scratched the surface. However, by understanding what these and other network security tools do, we can begin our journey of learning how to identify, remediate, and monitor potential attack vectors. It’s relieving to realize that defense doesn’t have to be manual. If you’d like to learn more about the career opportunities of ethical hacking and what positions employ these job responsibilities, then let’s talk about your approach to becoming a Certified Ethical Hacker.